As cloud adoption expands, companies/organizations will likely expose their data to risks. Adopting secure authentication to Azure resources is critical to prevent any security breaches.
Microsoft Azure already has an in-built identity and access service offering – Azure Active Directory (Azure AD).
Now, with the help of this blog, you will be able to grasp the concepts of Azure AD and explore the relationship between Azure Subscriptions and Azure AD.
A brief overview of Azure Active Directory
Azure AD is an Identity & Access Management (IAM) service. While we get into further details, here is one fundamental concept to understand – the Azure Tenant, an instance of Azure AD, which is automatically created when you sign up for an Azure Subscription.
So, an Azure AD can have a single-tenant (access resources of a single organization) or multi-tenant (two or more organizations), where Azure allows you to switch between Tenants depending on your Azure AD roles.
Why should you use Azure Active Directory?
Secured access to Azure services and applications is one of the advantages of using Azure AD.
To point out a real-world scenario, users would need to access different Azure services, where Azure administrators should create separate user ids and passwords for each of those services.
Here is where Azure Active Directory (AD) can be beneficial with its support for Single Sign-on access (SSO) – it helps users to access multiple services with a single set of login credentials.
Here are a few other attractive features offered by Azure AD;
- Azure AD supports 2 step verification for authentication, providing additional security to user sign-ins (multi-factor authentication).
- With distinctive identity protection capabilities, access security can be enhanced. It will also be possible to view suspicious sign-in behaviors and potential vulnerabilities.
- Dynamic groups in Azure AD help access users based on attributes like department, employee type, location, etc.
- It offers self-service capabilities for password management and re-setting, eventually improving security.
Let’s quickly look into what Azure Subscriptions are before we explore how they relate to Azure AD.
What are Azure Subscriptions & how to effectively use them?
An Azure Subscription is a logical container into which multiple Azure services can be configured. The billing/costs incurred by the services are determined at the Subscription level.
Depending on organizational needs, you can also have multiple subscriptions, each of which will have a unique Subscription ID.
Pros of having multiple Azure Subscriptions
- Consider a scenario where you must use various Azure services at different stages, such as testing/UAT, development, and production. In such cases, it would be preferable to have dedicated Azure Subscriptions.
- It makes it simple to view billing for each Subscription and set access restrictions for the Azure services configured in that Subscription.
- Organizations also typically use multiple Azure Subscriptions to get around per-subscription resource limitations.
Most businesses nowadays have more than a single Subscription, considering the pros.
One thing to notice here is an Azure Tenant also doesn’t restrict to having just one Azure Subscription associated with it (One Azure Tenant can have multiple Subscriptions).
How do Azure Subscriptions relate to an Azure AD instance (Tenant)?
A one-to-one trust relationship exists between an Azure Subscription and an Azure AD Tenant. A Subscription, in this case, trusts Azure AD to authenticate users, services & applications. As stated earlier, multiple Subscriptions can trust the same Azure AD Tenant, whereas each Subscription can only trust a single Tenant.
When a Subscription expires, the trusted instance remains the same, and only the security principal (user identity to access Subscription) can no longer access the resources associated with that Subscription.
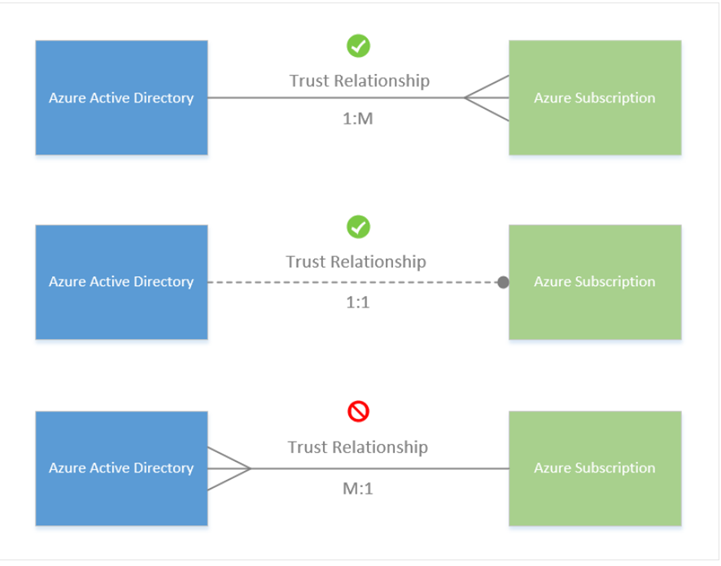
Additionally, your organization may have multiple Azure AD Tenants for different environments, such as UAT/Dev/Prod.
So, to make management more accessible, you would want to move a Subscription from one Tenant to another – this can only be done if you have owner-level access to the Subscription.
Areas to be considered while transferring Azure Subscriptions;
- Access will be revoked for users accessing Azure resources using Azure RBAC.
- Classic Subscription admin roles (Service Administrator & Co-Administrators) will also lose access.
- The Key Vaults will become inaccessible, so you must fix them after transferring the Subscriptions.
- If you have any managed identities for resources like Virtual Machines/Logic Apps, you must re-enable or recreate them, transferring the Subscriptions to a new Tenant.
How to restrict access to resources within an Azure Subscription?
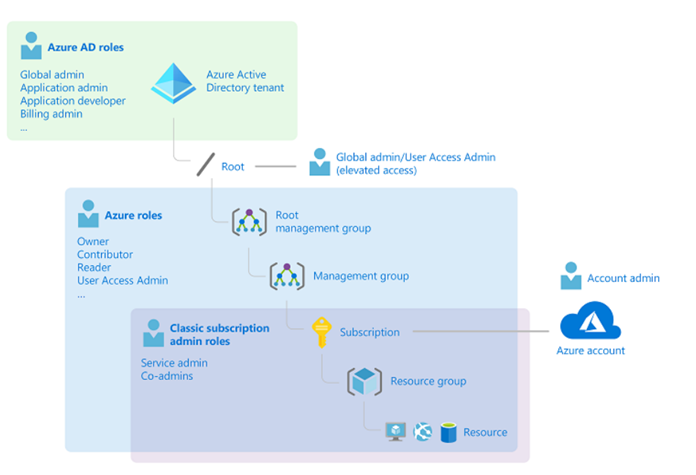
An Azure Subscription mainly trusts an Azure AD Tenant to enable Role-based access control (RBAC). So, to manage/access any resource in a particular Subscription, the user should have an account in the associated Azure AD Tenant.
With that, you can easily assign roles to security principals in an Azure AD at a specific scope to enable secured access to resources within a Subscription.
Here are the three roles you should be aware of to implement RBAC in Azure AD and at Subscription-level – Classic subscription administrator roles, Azure roles, and Azure AD roles.
But here are a few pitfalls in Azure RBAC,
- It doesn’t allow administrators to set up role-based access control on an application-level
- Azure RBAC supports access restrictions only for the Service Bus namespace and not for individual components like Queues, Topics & Subscriptions.
- It also just allows defining a certain number of custom roles per Azure AD.
In that case, it is recommended to use Serverless360 (Cloud management platform) for managing and monitoring Azure resources, as they provide more simplified & advanced RBAC.
Conclusion
I hope the blog gave you a clear picture of the fundamentals of Azure Active Directory (Azure AD) and Azure Subscriptions & pointed out the way they relate to each other with a trust relationship. We also discussed how Subscriptions could be moved between Tenants and how Azure AD ensured secured access to resources in Subscriptions.
Let’s consider your Azure Subscription has multiple Azure services like Service Bus, Storage Account, Cosmos DB, etc. Then managing them requires switching between Service Bus Explorer, Cosmos DB Explorer, Storage Explorer, or other management tools.
This limitation can be eliminated using Cerebrata (a cross-platform Azure management tool), which elevates management for various Azure services through one single interface.
