In this post we are going to talk about a very important and useful feature in Cerebrata that can help you prevent from accidentally deleting or updating your Azure resources that you manage through the tool.
Access Permissions
Access Permission is a unique feature in Cerebrata that can help you from accidentally deleting or updating your Azure resources that you manage through the tool.
These permissions can be specified only at the top hierarchy level (for example, in Storage Accounts the permissions can be specified at the connected storage account level and not at the blob containers or file share resources which the storage account possess), but these permissions can be specified with the resources that are added in the favourites folder.
Read Only
In Cerebrata, Read-only is a permission type which only allows a user to view the contents of the resource and restricting any writing to the resources. Setting a resource to “read-only” will still allow that resource to be opened and read. However changes such as new resource updation, creations, deletions, overwrites, edits or renaming cannot be made. This is often used to keep the users from making accidental updates and deletes.
Read Write
It is a permission type which allows a user to view and edit contents of the resources. This permission access allows you to upload or create new resource, whereas all the updation of the resources can also be made. The only restriction proposed with this permission is that you will be restricted from deleting the newly created as well as already available resources.
Full
It is a type of access permission which gives the user a complete control over the resources. The user can read or create any resource also the updation and deletion of the resources are also possible with this type of access permission.
How to set Access Permissions
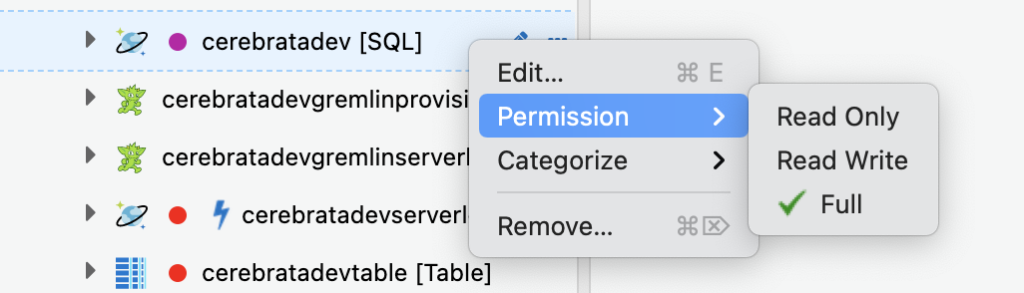
By default, Cerebrata allows the resources to be accessed with “Full” permission.To change the access permission in cerebrata, user should navigate to their desired connected resource -> click the (“…”) icon in connected resource -> click Permissions -> choose the access permission type. In Favourites folder user can click the (“…”) icon in any resource and can select the permission option to specify the access permissions.
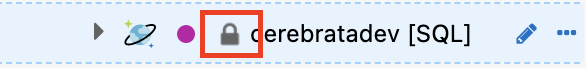
Following screenshots show how you can set permission on a resource in Cerebrata and how to visually identify if a resource is locked with “Read Only” or “Read Write” permissions.
Conclusion
In this blog, we understood how Cerebrata can be used to protect your Azure resources from accidental deletes and updates.
Cerebrata enables you to manage your Azure Cosmos DB accounts (SQL API, Gremlin API and Table API), Service Bus Namespaces, Cognitive Search Service accounts, Redis Cache accounts, and much more. It is also cross-platform so that you can manage your Azure resources from a platform of your choice – Windows, Mac, or Linux.
If you wish to experience Cerebreta, try our 15 days free trial.
